vShield Zones
vShield Zones is an application - aware firewall built for VMware vCenter Server integration. vShield Zones is a critical security component for protecting virtualized datacenters from attacks and misuse helping you achieve your compliance - mandated goals.
VMware is aware of the face that security is the foremost concern in all datacenters. VMware vSphere offers a unique virtual networking functionality called vShield Zones. vShield zone builds upon vSphere's virtual networking functionality to add virtual firewall functionality.
The critical network functionality allows administrators to observe and manage network traffic flows occurring between virtual network switches. Administrators can apply network security policies across entire groups of virtual machines, ensuring that these policies are managed properly even when the virtual machines are moved from host to another using VMware vMotion and VMware DRS.
vShield Zones includes components and services essential for analyzing traffic and protecting virtual machines. vShield Zones can be configured through a Web - based user interface and a command line interface (CLI). vShield Zones components are packaged as Open Virtualization Format (OVF) files. To run vShield Zones, you need one vShield Manager OVF and one vShield OVF.
vShield Manager
The vShield Manager is the centralized network management component of vShield Zones, and is installed as a virtual machine on any ESX host in your vCenter Server environment. A vShield Manager can run on a different ESX host from your vShield instances.
You can access the vShield Manager user interface by using a Web browser. The user interface lets administrators install, configure, and maintain the entire vShield Zones deployment. The vShield Manager User interface leverages the VMware Infrastructure SDK to display a copy of the vSphere Client inventory panel, and includes the Hosts & Clusters and Networks views. You can connect to the vShield Manager user interface using one of the following supported Web browsers:
Internet Explorer 5.x and later
Mozilla Firefox 1.x and later
Safari 1.x or 2.x
vShield
The vShield is the active security component of vShield Zones. Each vShield instance provides application - aware traffic analysis and stateful firewall protection by inspecting network traffic and determining access based on a set of rules. A vShield regulates traffic based on zones of trust, separating traffic into unprotected and protected zones. The virtual machines protected by a vShield reside in the protected zone. All traffic destined for the protected virtual machines enters from the unprotected zone.
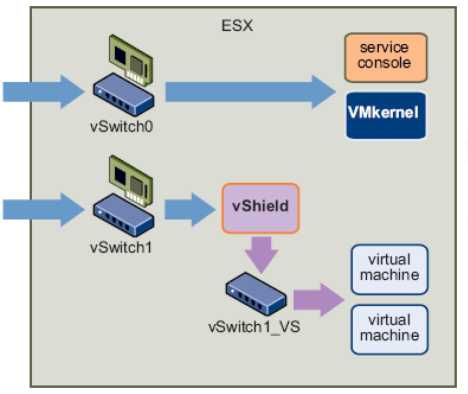
Installation of a vshield on a virtual switch
Using the vSphere Client, you can install the vShield OVF file as a template or virtual machine. After the package is installed in the vSphere Client, you use the vShield Manager to complete installation. If you installed the vShield package as a template, you can reference the template from the vShield Manager to install multiple vShield instances as virtual machines into your vCenter Server environment. You can install a vShield instance on any vSwitch that homes a physical NIC. As an ESX host can have multiple physical NICs, you can install multiple vShield instances on a single ESX host. When installed from a referenced template, the vShield installation process performs the following steps:
Creates a clone of the vSwitch host. This vSwitch clone does not include a NIC. The name of the vSwitch clone includes the name of the
vSwitch host with _VS appended: vSwitch1_VS.
Creates a protected zone port group, VSprotvShield - name, and attaches this port group to the vSwitch host.
Creates a management port group, VSmgmt_vShield - name, on the vSwitch host for the vShield instance's management interface.
Creates an unprotected zone port group, VSunprot_vShield - name, and attaches this port group to the vSwitch clone.
Connects and powers on the vShield instance.
Attaches the virtual interfaces on the vShield to the unprotected and protected port groups.
Moves the virtual machines from the vSwitch host to the vSwitch clone.
If the vShield Manager virtual machine resides on the same vSwitch, it is not moved. During vShield
Manager installation, you created a port group called vsmgmt in which to place the vShield Manager. vShield installation recognizes this port group name and ignores any virtual machines in this port group.
