The Security Perimeter
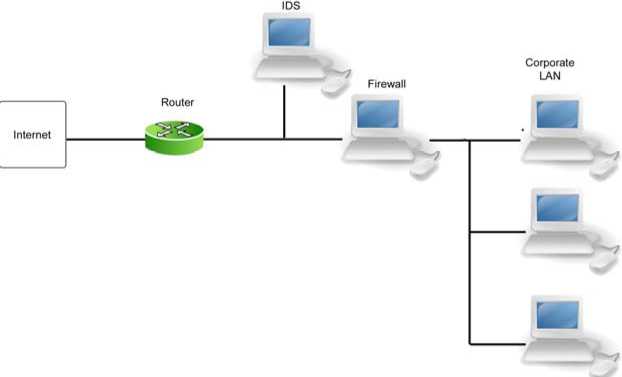
The discussion to this point has not mentioned the specific technology used to enforce operational and organizational security or a description of the various components that constitute the organization's security perimeter. If the average administrator were asked to draw a diagram depicting the various components of her network, the diagram would probably look something like Figure 2-1.
This diagram includes the major components typically found in a network. A connection to the Internet generally has some sort of protection attached to it such as a firewall. An intrusion detection system (IDS), also often a part of
Figure 2-1
the security perimeter for the organization, can be on the inside of the firewall, or the outside or it may in fact be on both sides. The specific location depends on the company and what it seeks to protect against (that is, insider threats or external threats). Beyond this security perimeter is the corporate LAN. Figure 2-1 is obviously a simple depiction-an actual network can have numerous subnets and extranets-but the basic components are present. Unfortunately, if this were the diagram provided by the administrator to show the organization's basic network structure, the administrator would have missed a very important component. A more astute administrator would provide a diagram more like Figure 2-2.
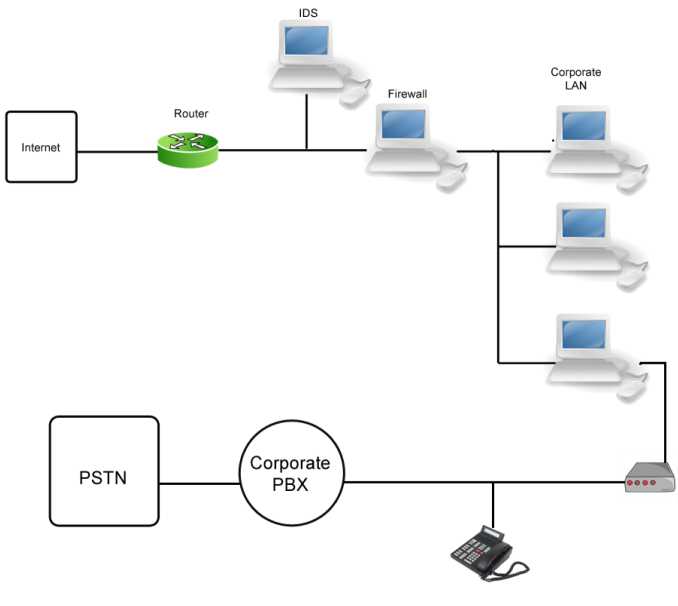
Figure 2.2
organization does not come from external attacks but rather from the insider-a disgruntled employee or somebody else who has physical access to the facility. Given physical access to an office, a knowledgeable attacker will quickly be able to find the information he needs to gain access to the organization's computer systems and network. Consequently, every organization also needs security policies, procedures, and guidelines that cover physical security and every security administrator should be concerned with these as well. While physical security (which can include such things as locks, cameras, guards and entry points, alarm systems, and physical barriers) will probably not fall under Leading the way in IT testing and certification tools, www.testking.com
This diagram includes the other important network found in every organization, the telephone network that is connected to the public switched telephone network (PSTN), otherwise known as the phone company. The organization may or may not have any authorized modems, but the savvy administrator would realize that because the potential exists for unauthorized modems, the telephone network must be included as a possible source of access for the network. When considering the policies, procedures, and guidelines needed to implement security for the organization, both networks need to be considered.
While Figure 2-2 provides a more comprehensive view of the various components that need to be protected, it is still incomplete. Most experts will agree that the biggest danger to any the purview of the security administrator, the operational state of the organization's physical security measures is just as important as many of the other network-centric measures.
