34 Explain the function of each layer of the OSI model
The OSI Model provides a structure that helps us to work with networks. The OSI Model 101, consists of seven layers. The services that can be availed of a network depend on the layer with which a device can be associated. A number is associated with every layer. The seven layers are:
- Layer 1: Physical Layer
- Layer 2: Data Link Layer
- Layer 3: Network Layer
- Layer 4: Transport Layer
- Layer 5: Session Layer
- Layer 6: Presentation Layer
- Layer 7: Application Layer
The figure given below illustrates the layers of the OSI model which are shown in the down up manner.
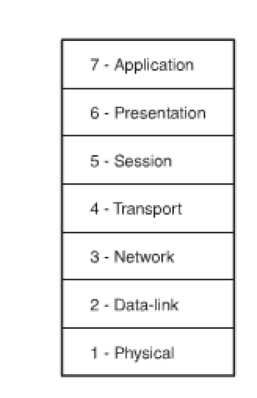
Figure 55: Layers of the OSI Model
The OSI model transports the data from one host to another. A piece of data that is forwarded from a web browser to a server, at the end of the sending device would have to travel down through all the layers and travel up through all the layers at the receiving end.
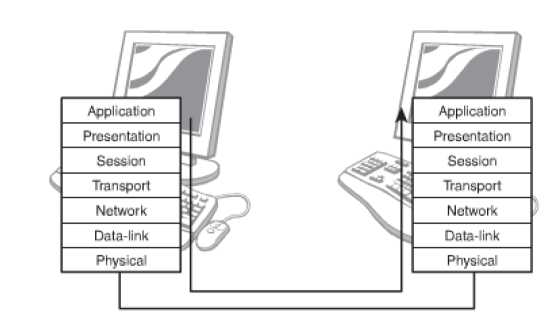
Figure 56: The course of Data in an OSI Model
While the data travels down the layers, headers are added which is known as encapsulation and removed as it travels down which is known as decapsulation. The figure given below illustrates the processes.
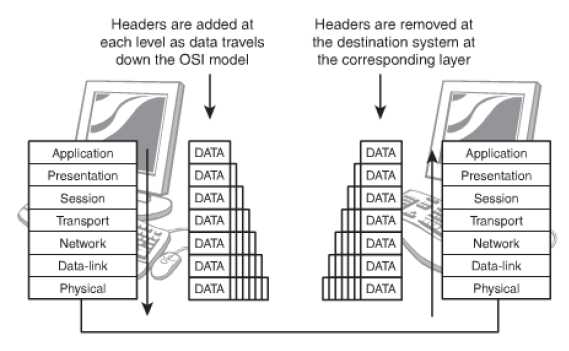
Figure 57: Encapsulation and Decapsulation
As the data travels down the decapsulation is done by the corresponding layer, which had added the information. With every movement of the information, it is sorted and arranged in logical groups of bits. A different term is used to define the process at every layer. The terms are:
|
Layer Name |
Term Used |
|---|---|
|
Layer 1 |
Bits |
|
Layer 2 |
Packets & Frames |
|
Layer 3 |
Packets & Datagrams |
|
Layer 4 |
Packets, Segments & Datagrams |
|
Layer 5 |
Packets |
|
Layer 6 |
Packets |
|
Layer 7 |
Packets & Messages |
Discussing the layers in detail:
Layer 1: The Physical Layer: This layer is used for defining the physical characteristics of the network. The physical characteristics refer to information about the type of connector to be used, the cable pin outs etc. Along with the topology, the course that the data will actually follow while traveling through the network is also determined by this layer. These factors have an impact on the speed of the media and the distance for which a media can be used effectively.
There are standards that can be even partially defined at the level of this layer. An example of a partially defined standard is the IEEE 802.3 Ethernet standard. Certain standards overlap over more than a single layer of the model.
Layer 2: The Data-Link Layer: The layer that sends the data or transmission to the physical layer is the data link layer. This layer performs checks and error detections on the data. It also ensures that the data sent and the data received is the same. The layer can be divided into two sub layers. The sub layers are:
- Logical Link Layer: The IEEE 802.2 standard defines this sub layer. This layer is responsible for controlling access to the media. The single network link is allowed to be used by multiple high level protocols. o Media Access Control: The MAC addresses are defined at the level of this sub layer. Access to the network media is managed by this sub layer.
Layer 3: The Network Layer: The responsibility of this layer is to equip the network with a mechanism that the data can move between two networks. It does prescribe the procedure of moving the data rather it concentrates on ensuring the mechanism for that purpose. It defines the network address and discovers the best route. The protocols followed at this layer are:
- IPX: This is a part of Novell's IPX/SPX protocol suite. It transmits the data using a connectionless transport mechanism.
- IP: This protocol is not much different from IPX when it comes to functions. The difference is that it forms a part of the TCP/IP protocol Suite
When a system tries to establish communication with another device that is present on the network, the identification of the device is done by the network. Once the system has been identified, it is time to access the services which is done by a service identifier. The ports in the case of TCP/IP protocols are referred to as Service identifiers and sockets in the case of Internetwork Packet Exchange/Sequenced Packet Exchange (IPX/SPX) networks are termed as service identifiers.
Switching Methods: Switching methods form a part of this layer. Switching methods are the techniques adopted to send data from one node to another. On various networks, three types of switching methods are used:
- Circuit Switching: This method creates a dedicated link between two points. The advantage of this method is that it is a point-to-point link it cannot be broken. The disadvantage is that data does not arise from a single source only.
- Message Switching: In this method, the data is broken down into smaller messages. It follows a store and forward policy. Before the data is hoped to the next switch it is temporarily stored in a node.
- Packet Switching: This is considered the best method for transmitting data. It breaks down the data into packets and these packets are moved around the network. A more comprehensive discussion of switching methods, in particular, how they relate to wide area networks, is included in Chapter 8, "Wide Area Networking."
Network Layer Addressing: Addressing is one of the most important functions that are undertaken in the network. As discussed earlier, the same is done by this layer. The Network Address is the logical address that which identify a system. This stands differently from the physically assigned MAC addresses, which are used on the data link layer. Because of these addresses, it is possible to approach addresses in a hierarchal and a logical approach. This further allows creation of subnets, which are groups of systems that are identified by a common address. Hierarchal addressing is not possible with non-routable networks.
Route selection is also made by this particular layer. Route selection means that selecting the best path that the data should take while moving in the network. Configuration of routes can be done in two ways:
- Statically: The addition of the routes to the routing table is done manually by the administrator while configuring statically.
- Dynamically: In this the addressing is left to be done automatically by routing protocols such as RIP (Routing Information Protocol) and OSPF (Open Shortest Path First).
Layer 4: The Transport Layer: The basic function that is performed by this layer is to transport data from one host to another. The actual processing of the data between devices is taken care of by this layer. Before sending the data, it segments it, and reassembles the data when it reaches the receiving end. Some of the errors can also be dealt with at this layer. The problems that it can handle are dropping of packets, duplication of packets, errors resulting from fragmentation and reassembly. The following protocols are used at the transport layer:
- TCP: It is a part of the TCP/IP protocol suite. This suite provides a connection oriented transport mechanism.
- User Datagram Protocol (UDP): This is also a part of the TCP/IP protocol suite. This also provides a connectionless transport mechanism.
- SPX: This is a part of Novell's IPX/SPX protocol suite; SPX provides a connection-oriented transport mechanism.
Connection-Oriented Protocols and Connectionless Protocols: There are two kinds of protocols- connectionless and connection oriented. In a connection-oriented protocol, the communication is established and maintained and once it is complete, the dialog between the two systems is broken down. The technical words used for the same are setting up and tearing down of a session. TCP is a connection-based protocol. The delivery of the data is guaranteed in this as every packet that is sent is acknowledged by the receiving system. This comes out as a reliable system of delivery. All packets that were not delivered are resent. Connection oriented protocols function at higher overhead costs than connectionless protocols.
Connectionless protocols do not work for assured delivery but rather they make the best efforts to deliver. They follow the fire and forget policy. The overheads of the protocols following this technique are much lower. The responsibility to ensure the delivery is on the higher layer.
Flow Control: Flow control is the acceptance of data and it also takes place at the level of the transport layer. It permits the acceptance of the data at a sufficient rate. The layer follows primarily two methods for flow control:
- Buffering: Buffering is the technique, wherein, data is temporarily stored in a holding area. It rests in this area till the destination device gives an
indication of being available. A problem occurs in this technique, if the sending device can send data at much faster rate than the acceptance rate of the receiving device.
- Windowing: It is a relatively better approach than buffering. The data is sent in a group and a single acknowledgment is required for the entire group. At the beginning of the session the size of the window (the number of segments that can be sent at one time) is set. This helps to lower the overheads.
Layer 5: The Session Layer: The layer that synchronizes the applications between two devices is the session layer. It manages the applications by establishing them and by breaking them as may be required.
Layer 6: The Presentation Layer: This layer converts the data that is received from an application layer to another format. Data is not always transmitted in a form readable by applications. The common data formats that are handled by the presentation layer are:
- Graphics files: JPEG, TIFF, GIF, formats in which graphic files can be stored. These formats need that the data be formatted in specific manner.
- Text and Data: This layer can translate data into different formats like American Standard Code for Information Interchange (ASCII) and Extended Binary Coded Decimal Interchange Code (EBCDIC).
- Sound/Video - MPEGs, QuickTime video these all files have data formats to which they have to be converted and reconverted.
Encryption is another function that is performed by the presentation layer. Encryption is the process of scrambling the data to make it unreadable for everyone and anyone other than the intended destination. The process of encryption is done at the sending end and the opposite that is decryption is done at the receiving end.
Layer 7: The Application Layer: This layer defines the processes allowing applications to use the devices placed on a network. Requests and data are taken from the user and passed on to the lower layers. This layer receives the incoming information which is later displayed to the user. The basic applications done by this layer are file and print options.
