16 Given a scenario, evaluate the proper use of the following addressing technologies.
There are various addressing technologies available. Looking at them in detail:
Subnetting: Subnetting is a process that uses the node portion of an address to create more networks. This allows more networks than the default subnet mask.
Lets us work with an example, A Class B address 150.150.0.0 is assigned and using the address and the default subnet mask, a single network is available. This would give multiple possibilities for node address. This node address is not very useful. Bits from the node portion can be borrowed to be used as a network address. The number of nodes per network is reduced but still there will be more than required. The simplest use to which subnetting can be put is to use a subnet mask of 255.255.255.0, instead of 255.255.0.0 which is the default Class B subnet mask. This gives 254 subnetworks and nodes amounting to 254 on each network.
In case more networks than 254 are required the process known as partial octet or fractional subnetting has to be used. In this, a part of the octet is used for the purposes of creating more networks, and the rest is left for assigning as node addresses. Continuing with the same example, in case six networks are to be created, enough bits need to be loaned from the third octet for creating six addresses. It is also required that as many node addresses as possible be also preserved. In case the first 3 bits are taken, a combination of the bits can be used to create values as the network addresses. The table given below illustrates the binary and the decimal values.
|
Binary Value |
Decimal Value |
|---|---|
|
000 |
0 |
|
001 |
32 |
|
010 |
64 |
|
011 |
96 |
|
100 |
128 |
|
101 |
160 |
|
110 |
192 |
|
111 |
224 |
Table 6: Values of Subnets Using 3 Bits from an Octet
The network assignments of 0 and 224 are not available as not portion of the address can be all 0's or all 1's. There are six possibilities of networks that are available.
The bits are taken from the left side of the octet. Addressing using subnetting makes it a complex issue to handle. Subnetting is undertaken for two reasons: First, the IP address range is used more effectively with subnetting and second, increased security and manageability is provided to create multiple networks. Multiple traffic types help to decongest traffic. This happens as the traffic is put only on that network for which it is meant.
Classless Interdomain Routing (CIDR): It is a method in which addresses are assigned outside the standard classes that is A, B and C. With the number of bits are specified in the subnet mask as a specific number, more flexibility is provided than it is available with the three standard class definitions. Values are assigned in this by using a value known as the slash. The value of the slash is controlled by the number of bits of the subnet mask that are used for expressing the network portion of the address. To explain with the help of examples, a subnet mask using all the 8 bits from the first octet and 4 from the second would be represented as 'A For representing a subnet mask that is using all the bits from the third octet would be /24
Network Address Translation NAT: the principle governing NAT is that many computer systems can take the shelter of a single IP address. This is done for the reason that there is a shortage of IP addresses. Using NAT, it becomes possible that one registered IP address is used on the external interface of the system. Between the internal and the external system, this system acts as a gateway. NAT allows the flexibility of exercising choice of addressing scheme on the internal networks.
When a NAT service is being performed, it funnels the requests that are made to it to the internet. A remote host takes the request to be from a single address. NAT keeps a record of the source of particular requests and returns the data received to the correct system. Servers providing NAT functionality keep a track of the source of request by statically mapping a particular internal address in relation to a specific external one. This ensures that the outgoing requests carry the same IP address. The figure given below illustrates the working of NAT.
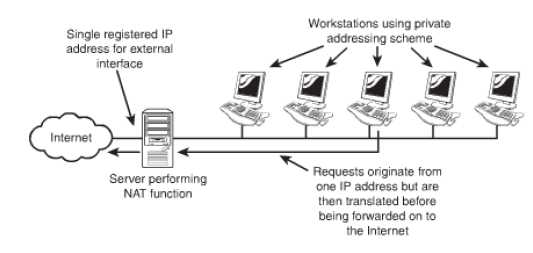
Figure 44: Working of NAT
There are few variations of NAT that are available, the variations are:
- PAT: PAT is a variation of NAT that ensures that all systems on the LAN are translated to an identical IP address but different port number. Incase of usage of the internet by multiple clients PAT can be used. There being a dearth of public IP addresses, it is required that the clients on the internal system be mapped to a single public IP address. Packets when received back into the private network are routed to their destinations after referring to a table within PAT. The table keeps a record of the public and private port numbers.
- SNAT and DNAT: SNAT and DNAT are variations of NAT. SNAT works by mapping a private IP address. It maps the address directly to a static unchanging public IP address. With this the internal system is able to have an unregistered private IP address. In spite of this it is still accessible over the internet.
In DNAT a private IP address is mapped to a public IP address. This is done using a cache of public IP addresses.
