13 Transmission Control Protocol /Internet Protocol (TCP/IP) Protocol Suite
The most striking feature of TCP IP is that only has it survived competition in this world of technology but has also been able to preserve its original state. With time dependency over TCP/IP has increased. TCP/IP is supportable by all the major network operating systems in use today.
TCP/IP is taken to be a single protocol but it is a TCP/IP suite and comprises of many protocols. Every function is catered to by an independent protocol and when they work together they are referred to as TCP/IP as commonly understood. The protocols cumulating to make the TCP/IP protocol suite are:
Internet Protocol (IP): The IP protocol, defined in RFC 791, is used for transporting data from one end to another. It is a connectionless protocol and works on the theory of best effort, that is, it will make the best effort to deliver the data but does not guarantee the delivery. To ensure completion of transmissions, TCP, which is a higher level protocol, is required. The IP protocol is also responsible for IP addressing.
Transmission Control Protocol (TCP): The TCP protocol is defined in RFC 793 and is a connection based protocol. It sets up sessions between two hosts before communication commences. It takes care of the reliability factor of IP communications. The other main features of this protocol are: controls flow of data, sequences data, detects errors and corrects. Applications of a higher level, that are looking for guaranteed delivery use TCP. The procedure is referred to as the three step handshake. The procedure followed by TCP is:
1. A message called SYN is sent to the target host.
2. A connection is opened by the target host. Once that is done an acknowledgment message called ACK or (SYN ACK) is sent.
3. The host that started the process sends back another acknowledgment. This acknowledgment says that the session is ready for transfer of data.
The procedure is repeated for closing the session. It is considered reliable as error detection and handling are incorporated in the protocol. It also has the facility of time outs, that is, retransmitting the data if the receipt is not acknowledged within a specified time.
User Datagram Protocol (UDP): The UDP protocol is defined in RFC 768, and is quite similar to TCP. The similarity is usage of IP as the transport protocol. It is a connectionless protocol
The differences are:
- Unlike TCP, it does not guarantee delivery. It is more of a fire and forget protocol, in the sense that it works on an assumption that data that has been sent will reach its destination.
- UDP leaves the checking whether the data has been received or not to the upper layer protocols.
- It does not establish a session between the sending and receiving hosts.
The advantage of UDP over TCP is:
- It has lower overhead than TCP. A UDP packet header has 4 fields as compared to a TCP which has 14. This makes it more efficient than TCP.
- It is more economical than TCP when it comes to bandwidth and effort put in for processing.
File Transfer Protocol (FTP): It is defined in RFC 959 and is a file transfer protocol. It enables uploading and downloading of files from a host which is remote. The prerequisite for this is it should have FTP server software. Along with this it allows viewing of the contents of the folders, renaming of files, deleting of files, in case the necessary permissions are there. IT uses TCP for transporting packets and hence looks for guaranteed delivery. It supports mechanisms for security which are used to authenticate users. FTP server software can be configured that allows anonymous logons. FTP servers offering files to the general public work by setting up anonymous logons. This makes it a popular choice for distributing files over the internet, for exchange of large files across a LAN. FFTP server capabilities are offered by the common network operating systems. The use of these facilities is a matter of personal choice. Usage of third party utilities like CuteFTP and SmartFTP is also common.
FTP works on the assumption that files that are to be uploaded and downloaded are text (ASCII) files. In case the files are not, the transfer mode has to be changed to binary. With utilities like CuteFTP, which are more sophisticated, the transition between transfer modes is automatic and with utilities which are more basic in nature, the switching has to be done manually. It is an application layer service that is resorted to often. Some of the commands used by command-line FTP client are:
|
Command |
Purpose of the Command |
|---|---|
|
Ls |
This command lists the files in the current directory on the remote system. |
|
Cd |
This command changes the working directory on the remote system. |
|
Lcd |
This command changes the working directory on the local host. |
|
Put |
This command uploads a single file to the remote host. |
|
Get |
This command uploads a single file to the remote host. |
|
Mput |
This command stands for multiple get and uploading of multiple files to a remote host. |
|
Mget |
This command downloads multiple files from the remote host. |
|
Binary |
Switches the transfer into the binary mode. |
|
ASCII |
Switches the transfers into the default mode, that is, the ASCII mode. |
Table 2: FTP Commands and their Purposes
Secure Shell (SSH): The secure shell is an effective alternative to Telnet. As the data travels between systems it is encrypted by this utility, hence it is a secure technique of transferring data. It is immune to packet sniffers and traffic detection systems. Over
Telnet authentication provided by secure shell is better. The two versions in which secure shell is available are:
- SSH1
- SSH2
SSH1 is a more secure version. The two versions are not compatible. It has to be ensured that the server implementation of SSH that is being connected to and the client SSH program are using the same version. Primarily SSH is linked with Unix and Linux, implementations of SSH are used for computing platforms and Windows. It forms the base technology for SFTP (Secure File Transfer Protocol)
Secure File Transfer Protocol (SFTP): FTP follows simple authentication methods, yet the network is not guarded effectively against even simple hacking approaches. FTP sends the data around in an unencrypted format rendering it to b copied easily. The solution to the shortcomings of FTP was SFTP. SFTP works by providing a more secure authentication between a sender and a receiver. It works by encrypting the data. The result is that even if a packet is copied from the network, its contents remain hidden. The implementation is done through client and server software.
Trivial File Transfer Protocol (TFTP): It is defined in RFC 1350. TFTP, a file transfer mechanism, is also a variation of FTP and used for simple downloads. It is neither as secure as FTP nor does it perform the functions at the same level. Unlike FTP which allows traversing across directories, TFTP does not allow this. For using TFTP it becomes necessary to specify the exact location and the request. For transporting data it uses UDP.
Simple Mail Transfer Protocol (SMTP): This protocol is used for defining how mail messages are to be exchanged between hosts. It uses TCP connections, guaranteeing an error-free delivery of messages. It is not a very sophisticated utility and has a shortcoming that the destination host has always to be available. The mail system spool the incoming mail and the users can access them later. The SMTP server controls how a user would read his mails later.
Hypertext Transfer Protocol (HTTP): It is the protocol allowing for text, graphics, multimedia, and other material to be downloaded. These downloads are allowed from an HTTP server. The actions that can be requested by the clients are defined by the server. The requests are issued by the clients in an HTTP format. These requests are made to HTTP server applications. HTML (Hyper Text Markup Files) files are created and returned to the client. Once the HTML file is returned the connection is closed.
The protocol uses a uniform resource locator (URL) to determine exactly which page has to be downloaded. The URL essentially comprises of the type of request (http:) and the server to be contacted. Mentioning the page is optional.
Hypertext Transfer Protocol Secure (HTTPS): In the HTTP protocol, requests are sent in clear text, which is not always suitable for applications like e-commerce, as it is not a secure method. The solution to this lay in the HTTPS protocol. The HTTPS protocol uses
SSL (Secure Socket Layer) for encrypting the information and forwarding the same between the client and the host. The prerequisite for this format to be used is that it should be supported by both the client and the server. The URL in this protocol starts with https
For HTTPS to be used, both the client and server must support it. All popular browsers now support HTTPS, as do web server products, such as Microsoft Internet Information Server (IIS), Apache, and almost all other web server applications that provide sensitive applications. When you are accessing an application that uses HTTPS, the URL starts with https: rather than http:
Access Protocol Version 4 (POP3/IMAP4): The protocol POP3 is defined in RFC 1939 and IMAP4 is defined in RFC 1731. Both are mechanisms for downloading, pulling emails from a server. This is a protocol that allows the mails to be stored as the user cannot always read them at the same time. POP and IMAP allow downloading and store the mail. Microsoft Outlook and Eudora are clients of POP and IMAP. The shortcoming of POP is that the password allowing access to the mailbox is transmitted across the network in a clear text. IMAP scores over POP on this aspect.
Telnet: The protocol is defined in RFC 854. It works as a virtual terminal protocol. It permits opening of sessions on a remote host and commands be executed on remote hosts. It was the system used for multiuser environments. It was also preferred for UNIX systems. Today its use is limited to accessing routers and other managed network devices. Security is compromised with Telnet protocol and the primary reason for the protocol to be replaced by SSH.
Internet Control Message Protocol (ICMP): It is defined in RFC 792. It is a protocol working with the IP layer providing for error checking and reporting functionality. It works on the best effort delivery. ICMP is used for a variety of functions, the most common being the ping utility. The ping utility sends a stream of echo requests to a host which is remote. In case the host is able to respond, it sends back an echo message to the host. The verification of the protocol suite of the sending node, the receiving node and devices lying in the path is done by one single and a simple process. Another important function that it performs is returning error messages like 'Destination Unreachable', 'Time Exceeded Messages'
Another important function performed by ICMP is source quench. In this situation the influx of data is not being dealt with at the same rate as it is being sent. The sending host has to be slowed down. The host node sends the source quench message, asking the sender node to slow down. This eliminates dropping of packets and the need to resend them. The ping utility is one the best utilities that it offers.
Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP): These protocols are defined in RFC 826 and RFC 903 respectively. This protocol resolves IP addresses to Media Access Control Addresses. When a system attempts to contact another host system, the first step that is undertaken is by the IP. It finds out if the system is on the same network or another. This is done from the IP address.
For a system on the local network, the ARP cache is consulted for the corresponding entry. In case the entry does not exist, in the ARP cache, a broadcast is made on the local network. The broadcast requests the host with the target IP address to transmit back its MAC address. The broadcast method is used to transmit this information as the source system in unable to communicate with the target directly. The broadcast reaches every system on the network, but the response is sent back only by the target. Once the target system recognizes the target of the ARP request, direct communication starts to take place between the two.
If the system is not present on the local system, but on a different subnet, the ARP process is done with the default gateway and repeated at every step that takes place while receiving and sending hosts.
Identical functions are performed by the Reverse Address Resolution Protocol (RARP) but as the name suggests in the reverse order. With RARP protocol applications and systems learn their IPS address from a router or DNS server
Network Time Protocol (NTP): The protocol is defined in RFC 1305 and its main function is to facilitate communication of time between systems. The working of this protocol is that one system is configured as a time provider and it transmits the information regarding the same to the other systems. These other systems are time receivers and at the same time be acting as time providers for other systems.
The distributed nature of applications makes it necessary to synchronize the time. External time sources like GPS and radio clocks may be a part of some environments. The BIOS clock of the system may be used in the others. For NTP time Internet based time servers are used as sources.
Network News Transfer Protocol (NNTP): It is defined in RFC 3977 and it uses TCP as its choice of transportation mechanism. It is a protocol that posts and retrieves messages from newsgroups. A discussion forum that is hosted on a remote system is termed as a newsgroup. Usage of NNETP client permits users to post, reply and retrieve messages. Newsgroups are fast being replaced by web based forums, but even then newsgroups are highly in demand. In NNTP retrieval of messages takes place from the server, and on the other hand in web based discussion forums the messages are not downloaded and are viewed from remote locations.
Secure Copy Protocol (SCP): This protocol is also based on SSH technology. The SCP protocol is rather a secure means of copying files between systems on a network. The data is encrypted by this protocol as it travels through the network. The data is secured against eavesdropping. SCP is more secure than RCP (Remote Copy Protocol). It is used a command line utility.
Lightweight Directory Access Protocol (LDAP): It is protocol providing for a mechanism permitting access and query directory service. For our reference the directory services are NDS (Novell Directory Services) and Microsoft Active Directory. Although LDAP supports command-line queries executed directly against the directory database, most LDAP interactions will be via utilities such as an authentication program (network logon) or locating a resource in the directory through a search utility.
Internet Group Management Protocol (IGMP): It is the protocol that manages the multicast groups in the TCP/IP protocol. It allows targeting of content to a specific group of computers which receive content from the sending system. Multicasting is directly opposite unicast messaging, in which data is forwarded to a single computer and not to a group or as a broadcast message. Multicasting as a mechanism allows techniques in which messages are not required to be sent to devices individuals but rather to groups of network devices at one particular time. In a group the devices are configured with an identical multicast address. The range of these addresses is from the IPv4 Class D including 224.0.0.0 to 239.255.255.255 address ranges. This also discovers other devices present on the network and sharing the same IP address, meaning that they are members of the same group.
Domain Name System (DNS): The protocol DNS performs one of the most important function on the TCP/IP suite, that is resolution of hostnames. It allows the users to refer to hosts by using easy to remember names rather than the IP addresses.
In days preceding the internet, the network used a text file which was called HOSTS. This was used for name resolutions and is required to be updated and distributed to other services very often. Using the HOSTS file was never an easy job and as the networks were expected to grow the process of maintaining the file would become all the more cumbersome. An automatic and a dynamic method was the need of the hour. The answer to the problem lay in DNS. The solution offered by DNS was to use servers configured to act as name servers. The DNS software permits receiving, processing and replying to the requests. These requests are issued from systems resolution of hostnames to IP addresses. Systems asking for resolution are termed as resolvers. The figure given below illustrates a resolution process.
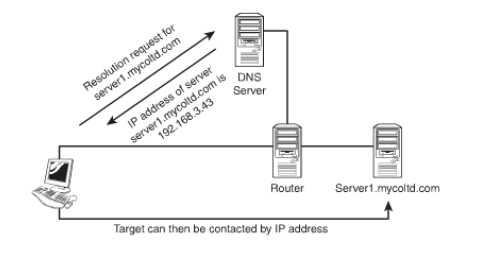
Figure 40: The DNS Resolution Process
It is not necessary that a DNS server will resolve every request. This happens for the reason that the quantum of the records is large enough to be held by a single server. In such a case the DNS server issues a request to another DNS server asking for an entry for the host.
The DNS Namespace: The DNS operates in a logical division that has been organized in a hierarchal structure and known as the DNS namespace. The top level is reserved for domain names such as .com, .edu, .uk etc. These are controlled and not open. Immediately following the top level are the sub domains, which are associated with companies like Microsoft, Red Hat. Further sub domains can be assigned in these. These are not controlled but rather open to use in the manner the user deems fit. The more commonly used domain names and their purposes are:
|
Domain Name |
Intended Purpose |
|---|---|
|
.com |
Commercial Organizations |
|
.edu |
Educational Organizations |
|
gov |
U.S. Governmental Organizations |
|
.mil |
Military |
|
.uk |
A country specific domain. (United Kingdom in this case) |
Table 3: Domain Names and their Associated Purposes.
DNS is an integral part of the internet. It is used of the ISP, if not of an individual. Internal DNS servers are resorted to incase of large and complex networks. The server applications are included by the vendors keeping future expansion of the system in mind.
Simple Network Management Protocol (SNMP): This is a protocol allowing network devices to pass on information about their state to a central system. In turn the central system passes configuration parameters to the devices.
Components of SNMP: A central system that is known as the manger acts as central point of communication for all devices that are SNMP enabled. SNMP software known as an SNMP agent needs to be installed and configured with an IP address on every device that has to be managed through SNMP. It is the configuration that determines with which devices the SNMP manager will communicate and retrieve information from. The agent communicates the occurrence of events to the manager as and when they happen. These messages are termed as traps. The figure given below illustrates the working of an SNMP.
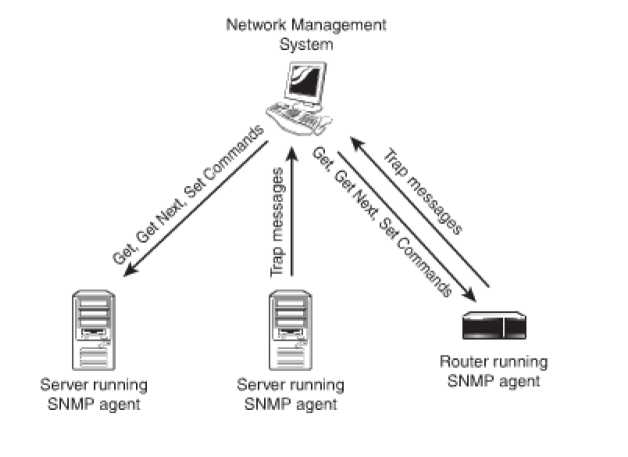
Figure 41: Working of SNMP
SNMP Management Systems: It is a computer that runs a special piece of software that is termed as network management system (NMS). The cost of these applications depends on the functionality and support provided by them. Most of the NMS software uses graphical maps of the network for locating a device and issuing queries to it. These queries are in built and be issued by a click. SNMP and NMS make monitoring of devices possible from a single location. It is a lot of power and so it has to be implemented in a secure workstation
SNMP Agents: An SNMP manager resides on a PC. Every device needs to be SNMP enabled. To achieve this, a software component known as agent is used. It is a device that can run small components of software facilitating communication with the manager. It also intimates with the SNMP managers every time anything goes wrong. A device running SNMP sends a trap to the NMS, when a certain condition is experienced. The action is then performed by the NMS. The actions that can be performed totally depend on the configuration.
SNMP Communities: SNMP communities are a logical grouping of systems. It simple means that when a system is configured as a part of a community, it would establish communication links with only those devices that share an identical community name. IT can accept commands like Get, Get Next, or Set from a manager with a community name that it recognizes. By default, two communities are defined: a read only community and a private community for the purposes of reading and writing. It proves useful as it can perform multiple functions.
Dynamic Host Configuration Protocol (DHCP): The protocol is defined in RFC 2131. It allows IP addresses to be defined in ranges. This is done on a system running a DHCP server application. The system asks for an address when a system that has been configured as a DHCP client is initialized. The address is assigned from the DHCP scope, for a definite period of time. This is known as a lease. The figure given below illustrates the working of a DHCP.
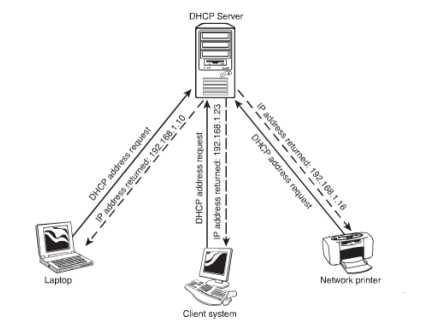
Figure 42: Working of DHCP
Time and again the lease is renewed. The lease expires when no renewal is possible. The DHCP server can supply more information than just IP address and the subnet mask. It depends on how the DHCP has been implemented. The other information that it can supply is the default gateway, the DNS information. It also performs the function of reservation. Reservation ensures that while using a DHCP the IP address remains the same.
The advantages of using DHCP are:
- Each system does not need to be configured manually.
- The probability of human error is eliminated.
- It is not necessary to reconfigure systems, while moving from one subnet to another in case of change of the IP addressing structure.
- It requires least amount of monitoring and maintenance.
The disadvantages of using DHCP are:
- It generates heavy network traffic as it is broadcast based.
- It has to be installed and configured on a server.
- The installation and configuring can be done on those systems which can support the load of an additional processor.
Transport Layer Security (TLS): This is a security protocol that has been designed for maintaining privacy, between communications taking place between client/server applications. It ensures that no eavesdropping takes place or nobody tampers with the data message. It is considered to be a successor of SSL.
Session Initiation Protocol (SIP): Voice over IP (VoIP) is a convenient and a cheaper option over regular telephones. Voice conversations take place by traveling through IP packets and the internet. For VoIP to work effectively, protocols are required. The protocol that is required is Session Initiation Protocol (SIP). SIP works as an application layer protocol and establishes multimedia sessions. It has the ability to create communication sessions for facilities like conferencing (video as well as audio) online gaming and one to one conversations. It uses TCP or UDP to transport data. When using TCP guaranteed delivery of packets is ensured, whereas with UDP this is not the case.
Real-time Transport Protocol (RTP): The protocols these days are expected to supported services such as video conferencing, VoIP etc. TCP and UDP protocols were not designed keeping the need of real time applications in mind. RTP was designed with eyes specifically set on these real time applications. It is known to be as a transport protocol but it rides often on UDP. With UDP, the delivery of the data is not guaranteed. UDP is preferred with RTP for the reason that it is less sensitive to loss of a packet but more to delays. It monitors delivery of data, look for packets that have been dropped, and carries data that has real time properties.
