50 Discuss various point-to-point authentication protocols uses in PPP
Point-to-Point is a protocol that provides layer 2 encapsulation. The key advantages of using PPP is that is provides authentication methods such as Password Authentication Protocol (PAP), Challenge Handshake Protocol (CHAP) and MS-CHAP. MS-CHAP is Microsoft proprietary version of CHAP protocol.
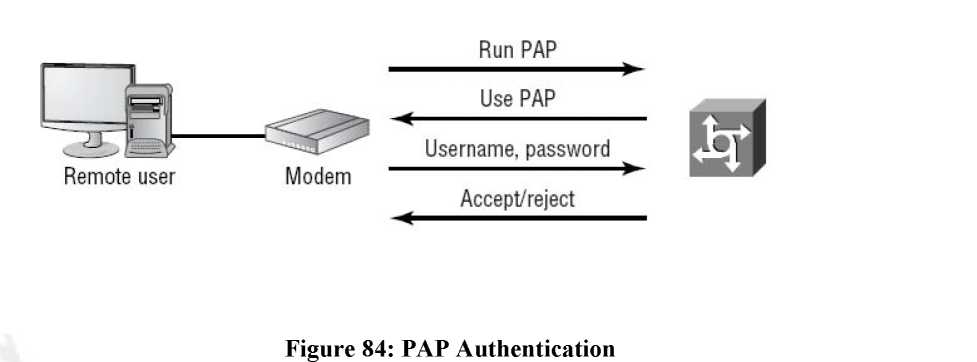
PAP
Password Authentication Protocol provides security authentication mechanism for links. After the initial PPP link has been established the two-way handshake is used by the client to verify its identity. The main disadvantage of PAP is that the username and password are sent in clear text format. As PAP imposes security vulnerabilities into the network it is not supported now days.
Working of PAP
In case of PAP firstly the link is established then the user sends their username/password for authentication after the authentication is complete the session is allowed.
Challenge Handshake Authentication Protocol (CHAP)
It is more secure than PAP. The username and the password sent by CHAP are encrypted. CHAP checks the identity of the user after some interval periodically. It uses the threeway handshake to perform this functionality.
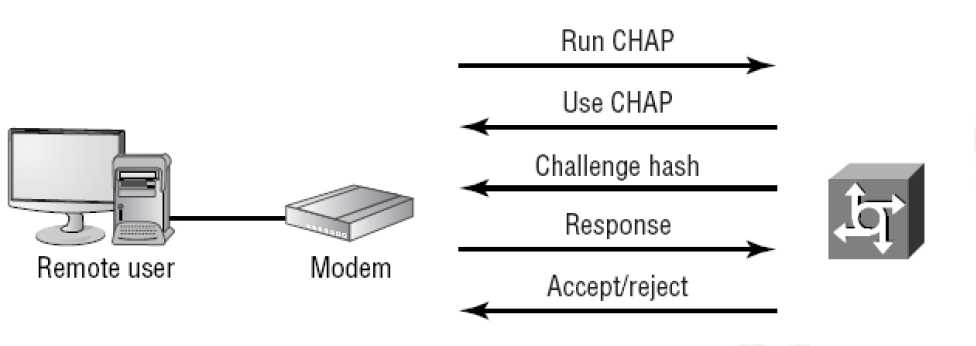
Figure 85: CHAP
MS-CHAP
It is the Microsoft version of CHAP called as MS-CHAP. It uses PPP authentication between a system running Microsoft operating system and NAS. There are several ways that the MS-CHAP differs from CHAP.
1) MS-CHAP response packets are compatible with Microsoft networking products.
2) MS-CHAP is enables after link establishment.
3) MS-CHAP can allow the remote client to change the MS-CHAP password.
4) In case of failed session there are various code that why the link establishment failed and these codes are then returned to the remote client by the NAS.
EAP
Extensible Authentication Protocol via the LANs
It is an authentication framework used in wireless networks. EAP can be used for wireless LANs as well as wired LANs. EAP is an authentication framework. There are various. It was developed to help two devices to negotiate. There are various types of EAP used today.
EAP-ESK
It is most popular form of authentication used in wireless networks. There is a shared key used between WAP and client. They are encrypted using powerful AES encryption.
Figure 86: Wireless Client and Access point
EAP-TLS
EAP along with the transport layer security defines the use of RADIUS as well as authentication requiring certificates on the server and client. It is used primarily on wireless networks and TLS is used on the secure websites.
EAP-TTLS
It is similar to TLS but it uses only single server side certificates as in case of EAP-TLS certificates are used on both sides.
EAP-MS-CHAPv2
It is known as PEAP. It uses a password function based on MS-CHAPv2 with the addition of an encrypted TLS tunnel similar to EAP-TLS.
EAP-MD5
This is simple version of EAP that uses MD5 for the transfer of authentication credentials. EAP-MD5 is weak as compared to other EAP methods.
LEAP
It is called as Lightweight Extensible Authentication Protocol (LEAP). It is Cisco proprietary EAP authentication used by Cisco wireless devices. LEAP is a combination of MS-CHAP and RADIUS server.
