48 Explain methods of user authentication Public Key Infrastructure (PKI)
It is used in case we want to want to work with someone whom we do not know. A certificate is a digital signature that includes the digital signature of third party. The entity that gives the certificate basically tells us that the person with whom we are communicating is actually the same intended person. Suppose we go to a shopping website xyz.com. The web server sends the copy of its certificate that certificate contains the web servers digital signature apart from that it contains the signature from the third party that verifies it is xyz.com. We can even see this certificate by clicking the lock icon on the bottom page of the browser.
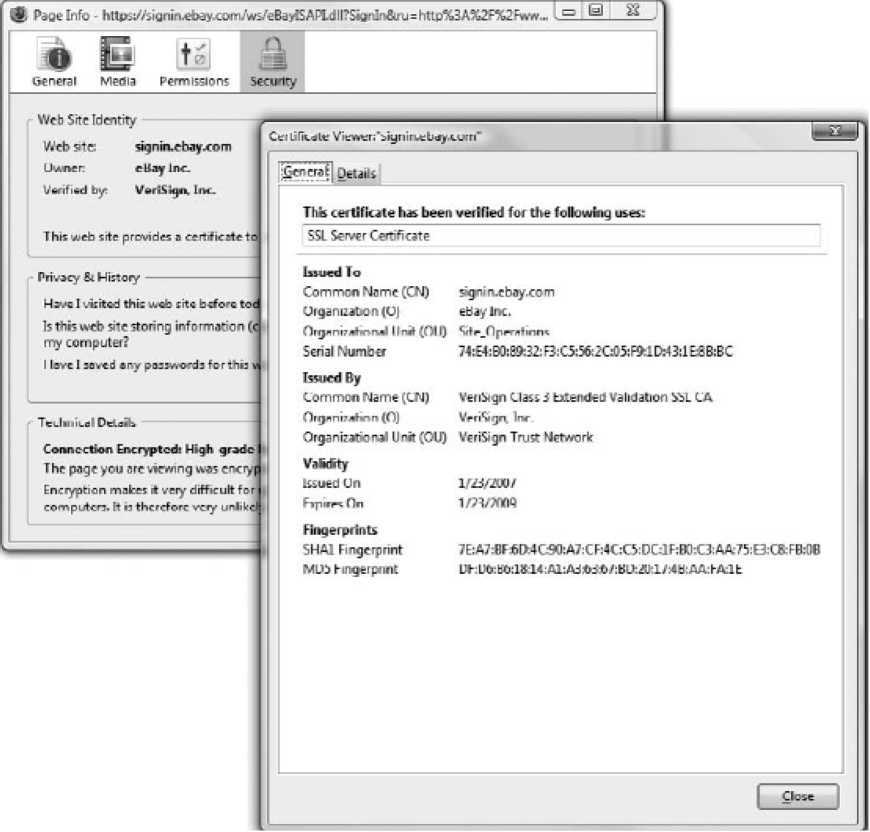
Figure 80: Digital Certificates
For example in the above figure VeriSign has issued this certificate. If someone creates a secure website he/she buys a certificate from the certificate authority. Various certificate authorities are available in the market today. The certificate providing authority acts as the root. Suppose the certificate issuing authority is VeriSign and it has placed certificate between VeriSign root certificate authority and user certificate. This structure will create a tree like structure where the certificate issuing authority sits at the top and the certificates that it issues are placed at the bottom. This structure is called as Public-Key Infrastructure (PKI).
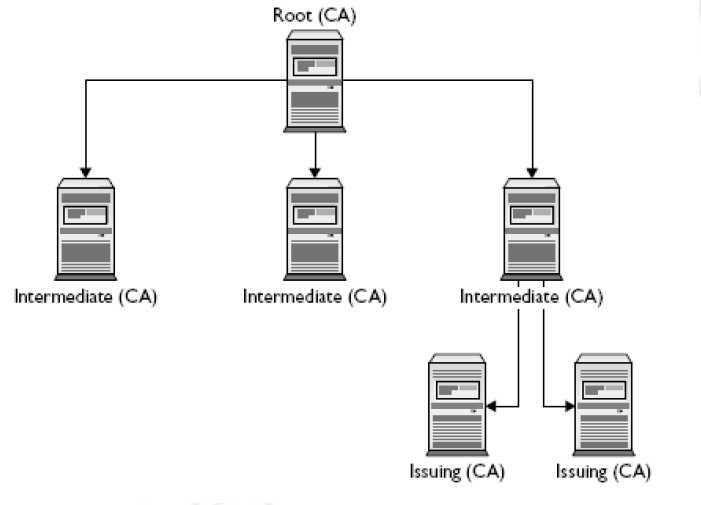
Figure 81: VeriSign PKI tree structure
Issuing (CA) Issuirg (CA)
Kerberos
Kerberos is an authentication and encryption method similar to RADIUS or TACACS+. It was developed at the Massachusetts Institute of Technology (MIT). It uses the same authentication mechanism as RADIUS and TACACS+ use the main difference is that after the user gets authenticated with Kerberos they are granted admission tickets. This ticket is used by the user to access various resources in the network without the need to enter their passwords again and again. The tickets that the Kerberos provides cannot be transferred or refunded. There is a limited time span of these tickets. After the admission ticket provided by the Kerberos has expired, the user needs to renew the ticket to access the network resources again. Kerberos is used by various devices. It is inbuilt in Windows 2000 and is implemented in Cisco routers. Until now it is the most secure method to authenticate the user.
