43 Explain the function of hardware and software security devices
Firewalls: They are used to protect the private network from unauthorized users on public network. Firewalls can be software or hardware based. Firewall i.e. hardware based has two network cards one that connects to the public network and other that connects to the private network. The packets that are coming from the outside/inside of the network are examined and in case there is a suspicious packet it is dropped.
Types of firewalls:
There are two types of firewalls such as: o Network based firewall o Host based firewall
Network based firewall
They firewall that uses a dedicated hardware to run is called as network based firewall. They are basically hardware based.
Host based firewall
The firewall that resides on computer is called as windows based firewall or host based firewalls. They are basically software based.
Intrusion Detection System
An IDS is a dedicated hardware based device that inspects incoming packets looking for intrusion. An ID monitors packets for viruses, illegal attempts in the network and other attacks.
There are two kinds of intrusion detection systems. o Network-based intrusion detection systems o Host-based intrusion detection systems
Network-based intrusion detection systems: They are deployed on the hardware. The location of network-based intrusion detection system is on the network edge.
Host-based intrusion detection systems: these systems do not need any dedicated hardware they can be deployed on the host based systems. They do not require any specific hardware for deployment.
Intrusion Prevention System
It is a device that monitors the network or suspected behavior and upon seeing any malicious activity it acts in real-time to prevent those activities. Network based intrusion prevention systems monitors the network and when they find any malicious activity they simply drop that packet but allow rest of the packets to travel through the network. Intrusion prevention system makes decision based on the content of the application rather than permitting or denying traffic based on IP addresses and port numbers. There are two kinds of intrusion prevention systems.
1) Host based intrusion prevention systems: It does not need is a dedicated hardware and they can be easily configured on a simple computer.
2) Network based intrusion prevention systems: It requires a dedicated hardware. They provide real-time security to the network.
VPN Concentrator
They are used to manage large number of remote sessions and also provide site to site connectivity. In case of large number of VPN sessions a simple computer cannot handle so VPN concentrators are used. For example Cisco VPN 3000 series concentrator is a widely used device.
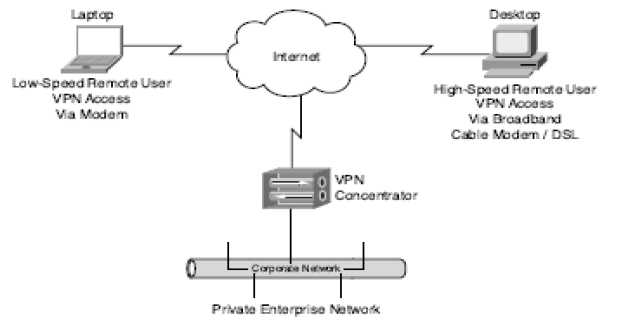
Figure 74: Cisco VPN 3000
VPN concentrators provide various features such as high-performance, security and fault tolerance. They save a large amount of money by allowing larger number of clients to access to the company's network through their local ISP. Some of the characteristics that make VPN concentrators popular are as follows:
1) Ease with which they can be deployed
2) Performance and scalability
3) Security
4) Fault tolerance
5) Management interface
6) Ease with which they can be upgraded
The majority of VPN concentrators support the following tunneling protocol:
1) Internet protocol security (IPsec)
2) Point-to-Point tunneling protocol
3) layer 2 tunneling protocol (L2TP)
4) L2TP/IPsec
5) Network Address Translation (NAT) transparent IPsec
