39 Given a scenario, select the appropriate command line interface tool and interpret the output to verify functionality.
It is important for a network administrator to learn how to use the TCP/IP utilities for troubleshooting processes. These utilities are one of the most common methods adopted to troubleshoot. These utilities are:
The ping Utility
It is a command line utility and on a network on the TCP/IP model it is used for testing connectivity between two systems. It is one of the most commonly and the first command used by an administrator. It uses the ICMP packets for checking connectivity between two systems. An ICMP echo request is forwarded to a remote host, in case the request is successfully received, the remote host replies with an ICMP echo reply in return and the ping is considered to be a success. The screenshot given below illustrates the output from a successful ping.

Figure: A successful ping request
The figure illustrated above shows the results of a successful ping on a Windows server system. In the above figure, four packets of 32 byte size each were forwarded to the remote host. 'The time = ' indicates the time taken to respond. If the time = is a higher number it means that there is traffic congestion. The above given figure is an indicator of a successful ping, which is not always the case. ping can fail also.
The ping command line utility offers several switches. Switches permit customization of the behavior of a command. The table given below illustrates the switches that are available with the ping command. These switches are available on a Windows Vista environment.
|
Switch |
Description |
|---|---|
|
-t |
It allows to ping a device on the network till specifically stopped. |
|
-a |
It allows the ping utility to resolve the IP address to a hostname as well as perform the ping simultaneously. |
|
-n count |
It specifies the number of ping requests that are to be sent to the remote host. |
|
-l size |
It specifies the buffer size of the ping request to be sent. |
|
-f |
Specifies that the Don't Fragment flag is sent in the packet |
|
-i TTL |
Specifies the time for which the packet can be alive |
|
-v TOS |
Specifies the type of service for the packet to be sent |
|
-r count |
Records the route hops that the packet takes on its journey |
|
-w timeout |
Specifies the time out in milliseconds |
|
- R |
Use routing header to test reverse route also (IPv6 only) |
|
-S scradder |
Source Address to use (IPv6 only) ' |
|
-4 |
Force using IPV4 |
|
-6 |
Force using IPv6 |
Table 11: Various Switches available with ping.
This being one of the most useful utilities available, it allows to isolate the problem and identify where exactly it lies. The following steps are to be taken while using ping:
1. . ping the IP address of your local loopback. This can be done by using the command ping 127.0. 0. 1. A successful ping would indicate correct installation of the TCP/IP protocol suite. In the other case TCP/IP would have to be reloaded or reconfigured.
2. . ping the IP address assigned to the local network interface card (NIC). A successful ping indicates that the interface is functioning properly. In the other case it indicates any one of the following:
- TCP/IP not bound properly to the NIC;
- Card drivers not installed properly;
- Computer not cabled properly.
To resolve this ping the IP address of another node which you are aware is working. This will help to find out if the system on which you are working is visible to the others. In case your system is not visible it could mean connectivity problems.
3. Verify connectivity to a remote network. This can be done by sending a ping to the IP address of the default gateway.
4. If step three fails, remote connectivity can be verified by sending a ping to the IP address of the system on a remote network.
The steps mentioned above not only help to verify connectivity on the local network but for remote networks also.
Ping Error Messages: Four error messages can be received back when ping is used. These messages are:
-
The Destination Host Unreachable Message: This message means that a route cannot be found to the specified destination. The message would look like:
Pinging 24. 67. 54. 233 with 32 bytes of data:
Destination host unreachable.
Destination host unreachable.
Destination host unreachable.
Destination host unreachable.
Ping statistics for 24.67. 54.233:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
Minimum = 0ms, Maximum = 0ms, Average = 0ms
-
The Request Timed Out Message: This error message means that the host did not receive back the ping message from the other host within the fixed time period. It indicates that there are connectivity issues with the destination device or that an intermediate device is not operating properly. This message can indicate traffic congestion and that the ping being sent to an invalid address as well. The output of this message would look like:
C: >ping 1 69. 76. 54. 3
Pinging 1 69. 76. 54. 3 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 169. 76.54. 3:
Packets: Sent = 4, Received = 0, Lost = 4 (100%
Approximate round trip times in milliseconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
-
The Unknown Host Message: This message is generated when the hostname of the destination computer cannot be resolved. This message is encountered when a ping has been sent to an incorrect hostname. It would look like:
C: >ping www.comptia.ca Unknown host www.comptia.ca
-
The Expired TTL Message: TTL performs an important function by checking for circular routing. It counts each hop that it experiences while moving towards the destination.
The traceroute Utility
Ping is a very strong utility but not sufficient for all times and situations. In situations where ping fails traceroute is resorted to. A TCP/IP utility, it traces the path taken by a packet to reach a remote host. In every network (LAN as well as WAN) there are multiple routes that a packet can take. The information on the routes is stored in a routing table. The packets are asked to take the route depending on the information contained in these routing tables and the utility tracert allows tracing the path, which a packet has taken while traversing through the network. The figure given below illustrates the results of a successful tracert command.

Figure 59: A successful tracert command
The tracert utility is used in combination with ping. The tracert utility is used first to determine, where the problem lies on a route and a subsequent use of ping allows determining the cause of the problem. Just as in the case of ping, even in tracert utility various switches are available. The table given below lists the various switches available on a Windows Vista System.
|
Switch |
Description |
|---|---|
|
-h |
Specifies the maximum number of hops to search for a target |
|
-d |
Do not resolve the addresses to the hostnames |
|
-w |
Specifies the wait time (in milliseconds) |
|
-R |
Traces the round trip path (IPv6 only) |
|
-4 |
Force using IPv4 |
|
-6 |
Force using IPv6 |
Table 12: Switches available with tracert command
The information that is derived from using the tracert command is IP address of every router and length of the round trip. An example of a successful tracert command on a Windows Server System
C: >tracert 24. 7. 70. 37
Tracing route to cl- p4.sttlwa1 .home. net [ over a maximum of 30 hops:
|
1 |
30 |
ms 20 ms |
20 |
ms 24.67. |
1 84. 1 | |
|
2 |
20 |
ms |
20 |
ms |
30 |
ms |
|
[24. |
67. 224. 7] | |||||
|
3 |
50 |
ms |
30 |
ms |
30 |
ms |
|
[204. 209. |
21 4. 1 93] | |||||
|
4 |
50 |
ms |
30 |
ms |
30 |
ms |
|
[204. 209. |
21 4. 90] | |||||
|
5 |
30 |
ms |
40 |
ms |
30 |
ms |
|
[66. |
1 63. |
76. 37] | ||||
|
6 |
30 |
ms |
40 |
ms |
30 |
ms |
Trace complete.
24. 7. 70. 37]
rd1ht-ge3-0. ok. shawcable. net rclwh-atmO- 2- 1 . vc. shawcable.net rc2wh-pos1 5-0. vc. shawcable. net rc2wt-pos2- 0. wa. shawcable. net cl -pos6-3. sttlwal . home. net [24. 7. 70.37]
The command can also be used to isolate a network with heavy traffic. To do this the command is generally run at different times of the day to find the rush hours. Successful commands during the night and unsuccessful commands during the day are clear indicators of high traffic during the day time.
The mtr Utility
The my traceroute or the mtr command is used on Linux/UNIX systems. On these systems it combines the work done by the ping utility and the traceroute utility. This command when issued gets the details of the path between two hosts. The pathping command does the same task in a windows environment.
The arp Utility
It is a part of the TCP/IP suite catering to resolution of IP addresses to MAC Addresses. This becomes essential as for low level communications MAC addresses are used. When communication has to be established between two systems, the IP addresses are used to locate each other. once that is done ARP requests sent and MAC address is ascertained. The utility is used for reviewing and modifying a host's ARP cache. The arp cache is the area in which ARP translations are stored. The ARP table contains information on static as well as dynamic entries. Static entries stay alive and can be appended manually using the -s switch. Dynamic entries get added as the system accesses other hosts on a network. The arp-a command opens the ARP cache. The figure given below illustrates the same.

Figure 60: The arp -a command
The switches associated with arp are given in the table below:
|
Switch |
Description |
|
-a (g) |
Used to display the current ARP entries. |
|
-d |
Do not resolve the addresses to the hostnames |
|
Inet addr |
Resolves MAC addresses of a remote system |
|
-N if addr |
Displays the ARP entries for a specific network interface |
|
-d inet addr |
Deletes entries from specified hosts |
|
-s inet-addr eth-addr |
Allows viewing of static entries in the ARP cache |
Table 13: Switches available with arp command The arp ping Utility
A ping request does not work with security measure like firewall as the ICMP requests are blocked by these. The arp ping utility is brought into use to check connectivity between devices in such a case. This utility uses ARP and not ICMP to check connectivity and works well on the local subnets. The arp ping in response send the MAC addresses and the name of the computer. This also helps to ascertain if duplicate IP addresses have been issued. It is not an inbuilt utility with windows but this utility can be easily downloaded. In the case of Linux it is a ready to use utility. The figure given below illustrates arp ping for a Windows set up.
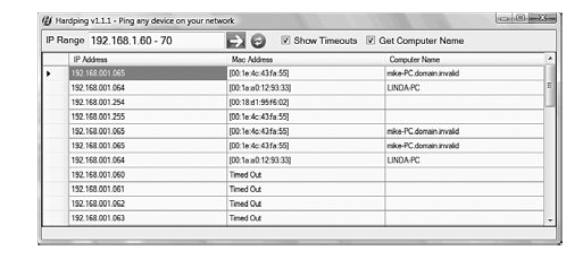
Figure 61: The arp ping command
The netstat Utility
This utility is used to display packet statistics in terms of packets sent and received, inbound TCP/IP connections, outbound TCP/IP connections. It provides more information than what ping can provide. The output from the command is displayed in the figure given below:

Figure 62: The Output from nestat command
There are a number of switches available with this command line utility too. The switches are:
|
Switch |
Description |
|---|---|
|
-a |
Lists the NetBIOS resolution table of a remote system identified by its hostname. |
|
-A |
Lists the NetBIOS resolution table for a remote system |
|
-c |
Lists the NetBIOS name cache along with the IP addresses |
|
-n |
Displays the NetBIOS local name tables |
|
-r |
Provides statistical information about resolutions |
|
-R |
Purges and reloads the NetBIOS names from the LMHOSTS file |
|
-S |
Displays the NetBIOS sessions table |
The nslookup and dig Utilities
These utilities are TCP/IP tools for troubleshooting DNS problems. These commands allow for interaction with the DNS server and location of records be performing manual DNS lookups. It is used in Window systems. The nslookup Utility allows running of manual name resolution queries against DNS servers, to derive information about DNS configuration and even kinds of DNS records that should be resolved. The figure given below illustrates the output of the nslookup command.

Figure 63: nslookup usage and its output.
The information that is derived by using this command occurs in two sections; first is the hostname and the DNS server that performed the resolution and second, is the domain name.

Figure 64: The nbstat command in Windows
The dig Utility is used in LINUX, UNIX environments. The command line can also be used to perform manual DNS lookups. It performs the same basic functions as nslookup. The figure given below illustrates the output of the dig command. It provides much more information than the nslookup command. It divides the information in three sections: the Answer Section -providing information about the domain name, host being resolved, IP address; Authority Section- providing information about authoritative DNS servers and the last four lines of the output showing the time taken to resolve along with the date and the time of making the request. The figure given below displays the output received from the command.

Figure 65: Output from dig command on a Linux system
The host Command
This command line is used on Linux/UNIX systems. It is used to carry out a reverse or a forward lookup on an IP address. A reverse lookup means resolving the hostname from the IP address. An example of the command line is:
host 24.67.108.119
It would return back the hostname associated with the IP address 24.67.108.119.
The route Utility
It is considered to be a very helpful tool. It displays and modifies the routing table. It works well for both Window systems and Linux systems. The figure given below illustrates an example of the command.

Figure 66: The output from a route print command on a Windows system
A number of switches are available with this command line. The options available are:
|
Switch |
Description |
|---|---|
|
Add |
Allows additions to be made to the routing table |
|
Delete |
Allows removal of routes to a routing table |
|
Change |
Allows modification of routing tables |
|
-p |
Usage of this with the add command makes the route persistent. |
|
|
Allows viewing of the routing table |
|
-f |
Removes gateway entries from the routing table |
Table 14: Switches available with route utility
