3 Explain common logical network topologies and their characteristics (Peer to peer, Client/server, VPN, VLAN)
As already discussed above a network is a group of connected computers and devices. The basic objective behind networking is to perform functions like communication and sharing of data and resources. Topology is the layout of a network. Broadly speaking, network topologies can be defined at two levels:
Physical Topology: This refers to the physical construction of a network. The same have already been discussed above.
Logical Topology: This refers to how a network functions.
Another way of classifying topologies is:
Wired Topologies
Wireless Topologies
The choice of network that is to be used by an organization depends on the role that the network is expected to play. Every model has its own set of advantages and disadvantages. The wired topologies use the following models:
Peer to Peer Networks: This is also referred to as a Work Group or a Decentralized Network. It is a low cost and an easy to implement network set up. It is suitable for small network environments which are required to share files and some hardware like a printer. All systems in this type of model are equal, and data is not stored centrally. The option of all users having complete access to their computers and other devices or not allowing access is there in this model. This model is ideal for set ups where the number of computers does not exceed ten. The figure given below illustrates a Peer to Peer Network.
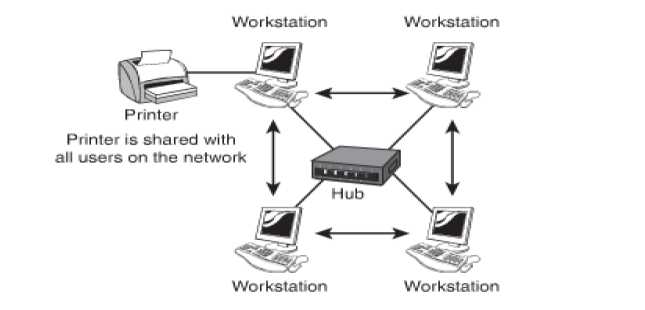
Figure 10: Peer to Peer Network Model
The main advantages of this model are: It is a cost effective set up and is easy to install and maintain. The disadvantages of this model are: It is a decentralized model and as a result the security of the network is jeopardized. Security has to be applied to each computer individually. There is no central data storage, therefore each system stores the data at its own end and as the number of computers and devices grows so does the complexity. It is fit only for a limited number of systems in a network.
The Client/Server Networking Model: This model is also called Server Based Networking. It uses a central set up in terms of security, network services and data storage. This network is most commonly used in the business world today. It is a scalable model meaning that it can be easily expanded. The figure below illustrates a Client Server Networking Model.
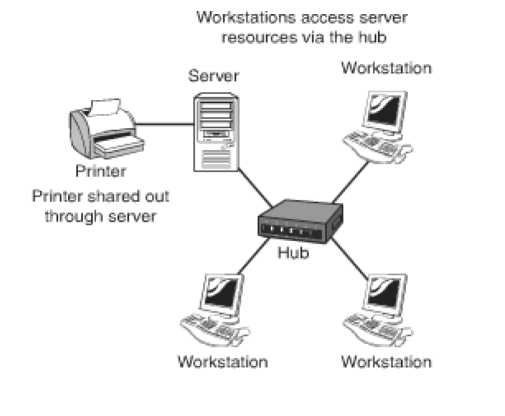
Figure 11: Client Server Network Model
There are two types of computers that are required for this model; these are servers and client computers. The advantages of this model are: a centralized security and data storage; easily expandable and ideal for larger number of systems. This model allows for expansion of the network with ease and is versatile. The disadvantages of this model are: It is not a cost effective model as it requires additional hardware as well as devices. The model needs administrative skills of a higher level for better management of the network. If the server fails the client's ability to access the services on the server are also effected.
Virtual Private Networks (VPN): A VPN is a model that extends a LAN. This is done be setting up a remote connection by using a public network. The model provides secure link between two points over a public IP network. The figure given below illustrates a VPN.
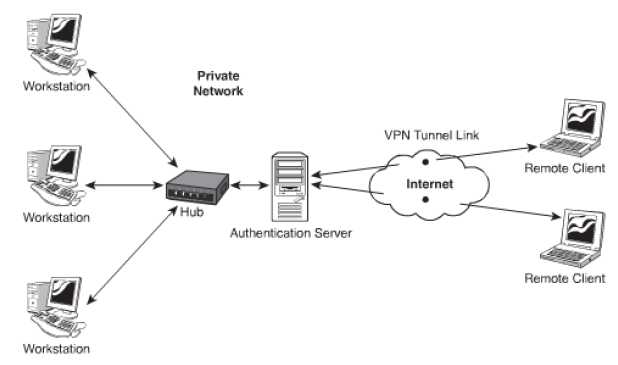
Figure 12: Virtual Private Network
The advantages of this model are: A cost effective model as it can replace remote access servers and dial up networks eliminating long distance phone charges. It is easy to expand without incorporating any modifications in the internal network structure. The model is easy to manage even without support staff for managing the network. Adding and removing clients from this model is easy. The disadvantages of this model are: The model is not secure as public network is being used. The model is dependent on the public network and as a result the system is not under the direct control of the organization.
Virtual Local Area Network (VLAN): This is a group of connected computers that act work in the same manner as they would in their own network segments. This model creates logical segments of a network as a result the administrator enjoys greater amount of flexibility beyond the physical design and infrastructure. It allows better management as the network is classified in sections. This model allows isolation of segments and hence is a more secure model. The advantages of this model are: It ensures an enhanced level of security. It reduces traffic that passes through the network. The job of the administrator becomes easy as the system is better organized. There are different methods to determine how devices are assigned in a specific VLAN. These are:
- Protocol Based VLAN's;
- Port Based VLAN's;
- MAC Address Based VLAN's
