Section 5.3: Authentication Technologies
Authentication techniques are the techniques that help you to identify people or systems what they claim to be. Authentication is one of the most important aspects to ensure secure infrastructure of your organization. Authentication works in conjunction with the identification. Where the identification enables a system to identify whether a user is known to the system, the authorization enables a system to find whether the user is allowed to access the requested resource or data. Identification, authentication, and authorization are often collectively referred to as access controls.
The three major factors on which authentication depend upon are:
1. Something you know: This may include Personal identification number (PIN) and password.
2. Something you have: This may include smart card and other identification devices as iButton.
3. Something physically unique about you: This may include your fingerprints or retinal patterns.
Some common Authentication methods used these days are:
- Username/Password: In this type of authentication, the user has to provide a user name and the password to a system in which it wants to log on. If the password matches the user is allowed to log on else not. This is one of the simplest, cheap, and most common types of authentication used these days but susceptible to many form of attacks. The passwords are generally vulnerable to guessing attacks and are subject to interception in transit over a network.
- Password Authentication Protocol (PAP): This is another simple form of authentication, which does not provide a strong authentication. Passwords and usernames in PAP are sent over the network for a match in text format and are vulnerable to sniffing attacks, as shown in Figure 69. This method is usually used where a plaintext password is required to simulate a login at a remote host.
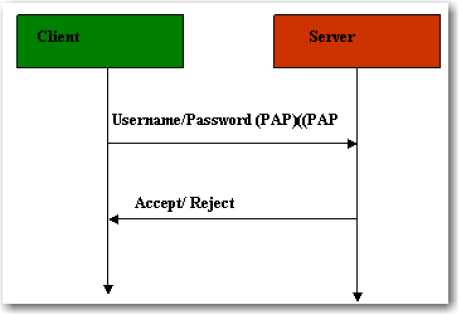
Figure 69
- Challenge Handshake Authentication Protocol (CHAP): Unlike PAP, CHAP is a stronger authentication method. It keeps verifying the identity of the peer periodically using a 3-way handshake after an initial link is established between the client and the server. It challenges a system to very identity. It does not use username/password for authentication rather the user sends a logon request from the client computer to the server and the server encrypts and sends the challenge back to the client, as shown in Figure 70. The client responds back with a value calculated using a "one-way hash" function. The server then checks the response from the client against its own calculation of the expected hash value. If the values matches, the authentication is granted else the connection is terminated.
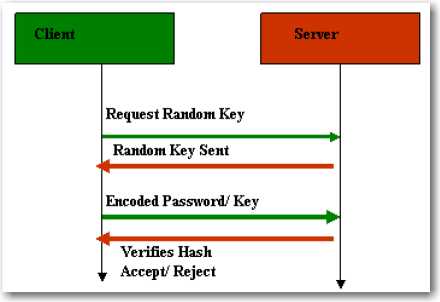
Figure 70
- Certificates: In this authentication method a digital certificate is issued by a server or a valid certification authority, which is accepted by the challenging system. These certificates can be used as a part of logon process to verify user identity for e-mail messages, e-commerce transactions, or smart cards. When applications encounter these certificates, they can check the authenticity of the certificate by inquiring with the issuing certificate authority to ensure the identity of the sender or website owner.
- Security Tokens: These are similar to certificates and can be used as software and hardware both to establish an identity of the user. A token is a piece of data that holds information about the user. The authentication system creates a security token every time a user connects or a session begins. The token is destroyed at the completion of the session.
- Kerberos: The Kerberos protocol has become a most common authentication method. It is a network-based authentication service and is used to provide single sign on to a distributed network. It provides tickets to the users as a proof of identity, after users are authenticated by presenting a user name and password for authentication. Each ticket issued by the Kerberos protocol has a start time and an expiration time. The ticket can be used as many times as necessary within that time frame.
- Smart cards: A smart card is a plastic card that resembles a credit card in size and shape. It has an embedded microprocessor that can be used to hold data. The smart cards are mainly used for identification, authentication, and data storage. They can be used for telephone calling, electronic cash payments, and for other similar applications. Smart cards provide a strong form of authentication when they are used for logging on to a domain because they use cryptography-based identification and proof of possession. Because smart card is a physical item, it can be stolen or lost. In that case the person who gets it can access all the resources it allows.
- Biometrics: Biometric authentication authenticates a person on the basis of the physical characteristics of the person. These characteristics are created when the person registers to the authentication system. It includes fingerprint recognition, iris recognition, retina recognition, and face recognition. Other biometric technologies include hand recognition, voice recognition, and signature dynamics. Biometric values of a person are verified for authentication and must be protected in transit if they need to be identified at a remote location.
Section 5.3.1: Multifactor Authentication
Multifactor authentication involves two or more methods of authentication. The example of two factor authentication can be the use of smartcards and the passwords both for the authentication.
